RMM and Vulnerability Scanning Strategies Unveiled
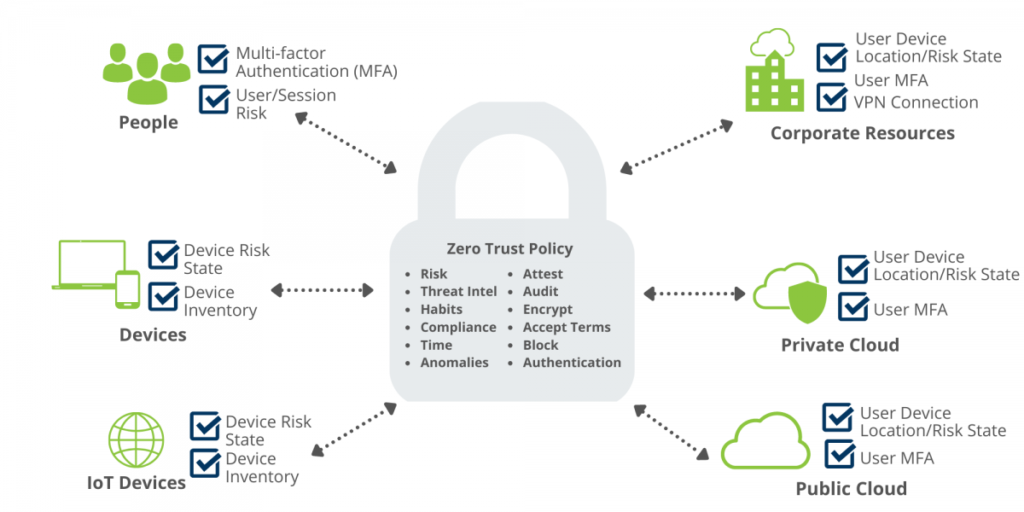
RMM and Vulnerability Scanning are integral components of modern cybersecurity, working in tandem to safeguard digital environments from evolving threats. By leveraging Remote Monitoring and Management tools alongside effective vulnerability scanning, organizations can proactively identify and mitigate potential security risks. Understanding the intricacies of these processes is essential for building a robust security framework that … Read more