RMM and Endpoint Security are crucial components in today’s digital landscape, where the threats to organizational integrity are ever-evolving. As businesses increasingly rely on technology, understanding the interplay between Remote Monitoring and Management (RMM) and endpoint security becomes essential. These tools not only streamline IT management but also fortify defenses against a myriad of cyber threats, ensuring a robust security posture.
RMM functions as a key player in IT management, allowing for real-time monitoring and maintenance of devices, while endpoint security focuses on protecting endpoints such as laptops and smartphones from malicious attacks. Together, they create a comprehensive security framework that safeguards sensitive information and enhances operational efficiency, making their integration vital for any modern enterprise.
RMM Overview

Remote Monitoring and Management (RMM) is a crucial aspect of IT management that enables organizations to monitor and manage their IT systems and infrastructure remotely. Its significance lies in enhancing operational efficiency, improving system uptime, and enabling proactive management of IT resources, ultimately leading to reduced costs and improved service delivery.RMM tools are designed with several key components that collectively enhance IT management capabilities.
When comparing RMM vs. Manual IT , it becomes clear that remote management tools offer significant advantages over traditional methods. RMM solutions provide automation and real-time monitoring, reducing the workload on IT teams and minimizing downtime, while manual approaches often lead to slower response times and increased risk of human error.
These tools typically include monitoring features that track system performance in real-time, alerting mechanisms to notify administrators of potential issues, and management functionalities that allow for remote access to devices for troubleshooting and maintenance purposes. Additionally, RMM solutions often integrate reporting and analytics capabilities to provide insights into system health and performance trends.
Main Components of RMM Tools
Understanding the main components of RMM tools is essential for leveraging their full potential in IT management. The effectiveness of RMM solutions is determined by the following core elements:
- Monitoring Agents: These software components are installed on devices to gather data about system performance, resource usage, and security compliance. They play a critical role in ensuring real-time visibility into all monitored systems.
- Dashboard Interface: A centralized platform that provides IT administrators with an overview of the health and status of all managed devices, enabling quick assessments and decisions.
- Alerting System: An essential feature that notifies IT staff of critical events or performance issues, ensuring prompt action to mitigate risks and resolve problems before they escalate.
- Remote Access Tools: These tools allow IT personnel to access and manage devices remotely, facilitating troubleshooting and maintenance without the need for on-site visits.
- Reporting and Analytics: RMM solutions often include analytics dashboards that provide insights into system performance, usage trends, and potential areas for improvement, assisting in strategic IT planning.
Advantages of Implementing RMM Solutions
Implementing RMM solutions offers numerous advantages that can transform how businesses manage their IT environments. The following points highlight the key benefits:
- Proactive Issue Resolution: RMM tools enable organizations to detect and address potential issues before they impact business operations, significantly reducing downtime and improving system reliability.
- Cost Efficiency: By automating routine IT tasks and facilitating remote support, RMM solutions can lower operational costs associated with on-site IT management and maintenance.
- Improved Security: Continuous monitoring and management of systems enhance security posture, allowing for timely updates and patch management to address vulnerabilities.
- Enhanced Productivity: With IT personnel able to manage systems remotely and efficiently, employees can focus on core tasks rather than IT-related disruptions.
- Scalability: RMM solutions can easily scale with business growth, allowing organizations to manage an increasing number of devices and resources without significant additional investment.
“RMM tools provide a strategic advantage in today’s fast-paced business environment, enabling organizations to maintain competitive edge through effective IT management.”
Endpoint Security Fundamentals
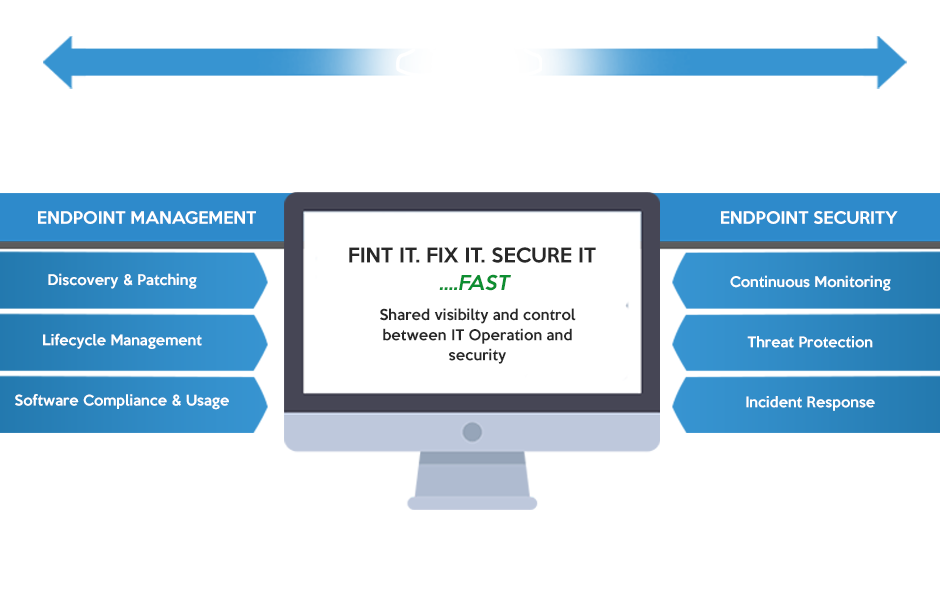
Endpoint security is the practice of securing endpoints or entry points of end-user devices such as desktops, laptops, and mobile devices from potential threats. The significance of endpoint security lies in its ability to protect organizational networks from breaches that can originate from these devices. With the rise of cyber threats and the increasing number of devices connecting to corporate networks, it has become essential for businesses to implement robust endpoint security measures.
Effective endpoint security solutions are designed to prevent, detect, and respond to various types of threats, thus safeguarding sensitive data and ensuring the integrity of organizational assets. The landscape of endpoint security is diverse, offering various solutions tailored to specific needs. Understanding these solutions and their role in protecting assets is vital for organizations looking to fortify their defenses.
Types of Endpoint Security Solutions
Numerous endpoint security solutions are available in the market, each offering unique features and capabilities. The variety caters to different organizational needs, ensuring that businesses can find a suitable option for their security posture. Key types of endpoint security solutions include:
- Antivirus and Antimalware: Traditional software designed to detect and remove malicious software, protecting endpoints from known threats.
- Endpoint Detection and Response (EDR): Advanced solutions that monitor endpoint activities in real-time to identify and respond to threats quickly.
- Data Loss Prevention (DLP): Solutions that prevent unauthorized data transmission outside the organization, ensuring sensitive information remains secure.
- Firewall Solutions: These create a barrier between trusted internal networks and untrusted external networks, controlling incoming and outgoing traffic.
- Mobile Device Management (MDM): Tools that manage and secure mobile devices used within an organization, focusing on access control and data protection.
- Unified Endpoint Management (UEM): A comprehensive approach that integrates management for all endpoints, ensuring consistency in security policies and procedures.
Role of Endpoint Security in Protecting Organizational Assets
The role of endpoint security in safeguarding organizational assets is multifaceted and critical. By offering various protective measures, endpoint security ensures that sensitive organizational data is defended against a plethora of cyber threats, including ransomware, phishing, and data breaches.Implementing endpoint security is crucial for several reasons:
- Protection Against Cyber Threats: With the increasing sophistication of cyberattacks, endpoint security solutions provide vital protection against evolving threats.
- Regulatory Compliance: Many industries are governed by regulations that mandate strict data protection measures; effective endpoint security helps ensure compliance.
- Data Integrity: Endpoint security helps maintain the integrity of organizational data by preventing unauthorized access and potential data loss.
- Enhanced Visibility: Solutions like EDR provide organizations with enhanced visibility into endpoint activities, enabling quicker identification of security incidents.
- Cost Efficiency: Investing in robust endpoint security can save organizations significant costs associated with data breaches and recovery efforts.
“Effective endpoint security is not just a protective measure; it is a fundamental component of an organization’s overall security strategy.”
Integrating RMM and PSA Integration enhances operational efficiency by allowing seamless data flow between remote monitoring management systems and professional services automation. This synergy not only streamlines workflows but also optimizes service delivery, ensuring that businesses can respond swiftly to client needs while maintaining high standards of performance.
Integration of RMM and Endpoint Security
The integration of Remote Monitoring and Management (RMM) tools with endpoint security solutions is increasingly crucial in today’s digital landscape. As businesses strive to protect their IT environments from evolving threats, the synergy between these two technologies offers enhanced visibility, control, and resilience against cyberattacks. This section delves into how RMM tools can bolster endpoint security measures, the challenges faced during integration, and a strategic approach to ensure effective collaboration.
Enhancement of Endpoint Security Measures through RMM Tools
RMM tools serve as a pivotal component of modern IT management, providing comprehensive monitoring and management capabilities that enhance endpoint security. By integrating RMM with endpoint security, organizations can achieve real-time visibility over their endpoints, enabling timely updates and patches, which are critical in mitigating security vulnerabilities. The key benefits of this integration include:
- Automated Patch Management: RMM tools can automate the deployment of security patches across all endpoints, significantly reducing the window of vulnerability.
- Centralized Monitoring: Continuous monitoring through RMM facilitates early detection of anomalies and potential threats, allowing for immediate remediation actions.
- Incident Response: RMM’s remote access capabilities allow IT teams to respond quickly to security incidents, minimizing damage and recovery time.
- Comprehensive Reporting: Integrating RMM with endpoint security provides detailed reports on security compliance and status, empowering organizations to make informed decisions.
Challenges in Integrating RMM and Endpoint Security Solutions
Despite the benefits, several challenges can arise when integrating RMM and endpoint security systems. Understanding these obstacles is essential for developing a robust integration strategy.Key challenges include:
- Compatibility Issues: Different RMM and security solutions may have compatibility issues, limiting their interoperability and effectiveness.
- Resource Allocation: Integrating these systems may require additional resources and expertise, which can strain IT teams.
- Data Overload: With enhanced visibility comes the challenge of managing large volumes of data, making it difficult to prioritize and address critical security issues effectively.
- User Training: Ensuring that personnel are adequately trained to utilize integrated systems can be a significant hurdle, affecting the overall effectiveness of the integration.
Strategy for Effective Integration of RMM with Endpoint Security
To maximize the benefits of integrating RMM and endpoint security solutions, organizations should adopt a strategic approach. This involves various steps that ensure seamless collaboration between the two systems.An effective integration strategy should include:
- Assessment of Current Environment: Conduct a thorough analysis of existing RMM and endpoint security systems to identify compatibility and integration opportunities.
- Vendor Collaboration: Work closely with vendors of both RMM and security solutions to ensure smooth integration and support for troubleshooting.
- Unified Dashboard Implementation: Develop a centralized dashboard that consolidates data from both systems, enabling easier monitoring and management.
- Regular Training Programs: Implement ongoing training for staff to keep them informed about best practices and updates related to integrated systems.
The successful integration of RMM and endpoint security ultimately leads to a fortified security posture, allowing organizations to stay ahead of threats while efficiently managing their IT resources.
Best Practices and Future Trends
In the rapidly evolving landscape of Remote Monitoring and Management (RMM) and endpoint security, staying ahead requires a proactive approach. Organizations must not only implement effective strategies but also anticipate future developments that could impact their operations. This section will explore best practices for managing RMM and endpoint security, predict future trends in these technologies, and highlight the significant role of artificial intelligence in enhancing security measures.
Best Practices for Managing RMM and Endpoint Security
To ensure the effectiveness of RMM and endpoint security, organizations should adopt several best practices. These practices help in minimizing vulnerabilities and enhancing overall security posture.
- Regular Updates and Patch Management: Keeping software up-to-date is crucial. Regularly applying patches to operating systems and applications reduces the risk of exploitation from known vulnerabilities.
- Comprehensive Asset Inventory: Maintaining an accurate inventory of all endpoints provides visibility into what needs monitoring and securing. This includes hardware, software, and network devices.
- Employee Training and Awareness: Investing in training programs helps employees recognize phishing attempts and other security threats. An informed workforce is the first line of defense against cyber attacks.
- Implementing Multi-Factor Authentication: Utilizing multi-factor authentication adds an additional layer of security, making it more difficult for unauthorized users to gain access to sensitive systems.
- Regular Security Audits: Conducting periodic security audits helps organizations identify potential weaknesses in their security infrastructure and rectify them proactively.
Future Trends in RMM and Endpoint Security Technologies
The future of RMM and endpoint security is poised to be influenced by several key trends. Recognizing these trends can help organizations prepare for upcoming challenges and opportunities.
- Increased Adoption of Cloud-Based Solutions: As businesses continue to migrate to cloud environments, RMM solutions are also expected to leverage cloud technologies, offering scalability and improved accessibility for remote management.
- Integration of Zero Trust Architecture: Implementing a zero-trust framework will become essential, as it assumes that threats could be internal or external, necessitating continuous verification for all users and devices.
- Expansion of Managed Security Service Providers (MSSP): The demand for outsourced security management is increasing as organizations seek specialized expertise to handle complex security challenges.
- Focus on User Behavior Analytics: Enhanced analytics capabilities will emerge, allowing organizations to monitor user behavior and detect anomalies that may indicate a breach.
- Regulatory Compliance Automation: As regulations evolve, automated compliance tools will gain traction, helping organizations ensure they meet legal requirements without excessive manual effort.
The Role of Artificial Intelligence in RMM and Endpoint Security
Artificial intelligence (AI) is transforming RMM and endpoint security by providing advanced capabilities that enhance threat detection, response, and overall security management.
- Automated Threat Detection: AI algorithms can analyze vast amounts of data to identify patterns indicative of cyber threats, allowing for quicker response times and minimizing damage.
- Predictive Analytics: AI can anticipate potential security breaches by analyzing historical data and identifying trends, enabling proactive measures before incidents occur.
- Enhanced Incident Response: Machine learning models can automate incident response processes, reducing the time required to react to threats and freeing up human resources for more strategic tasks.
- Adaptive Security Measures: AI systems can continuously learn and adapt to new threats, ensuring that security measures evolve in real-time to address emerging vulnerabilities.
- Improved User Experience: By streamlining security processes and minimizing false positives, AI contributes to a better user experience while maintaining robust security standards.