Remote Access in RMM plays a crucial role in today’s fast-paced digital landscape, enabling organizations to streamline their IT support operations. As businesses increasingly rely on technology, the ability to access systems remotely not only enhances operational efficiency but also ensures quicker response times to technical issues. With the right remote access solutions, teams can not only diagnose and resolve problems from afar but also do so with heightened security considerations in mind.
The significance of remote access is underscored by its ability to bridge the gap between IT personnel and the systems they manage, allowing for real-time interventions without physical presence. This capability is vital for maintaining productivity and minimizing downtime, especially in an era where remote work is becoming the norm. Exploring the various tools and technologies available for remote access, along with best practices for implementation, reveals a pathway to optimizing IT support in any organization.
Importance of Remote Access in RMM
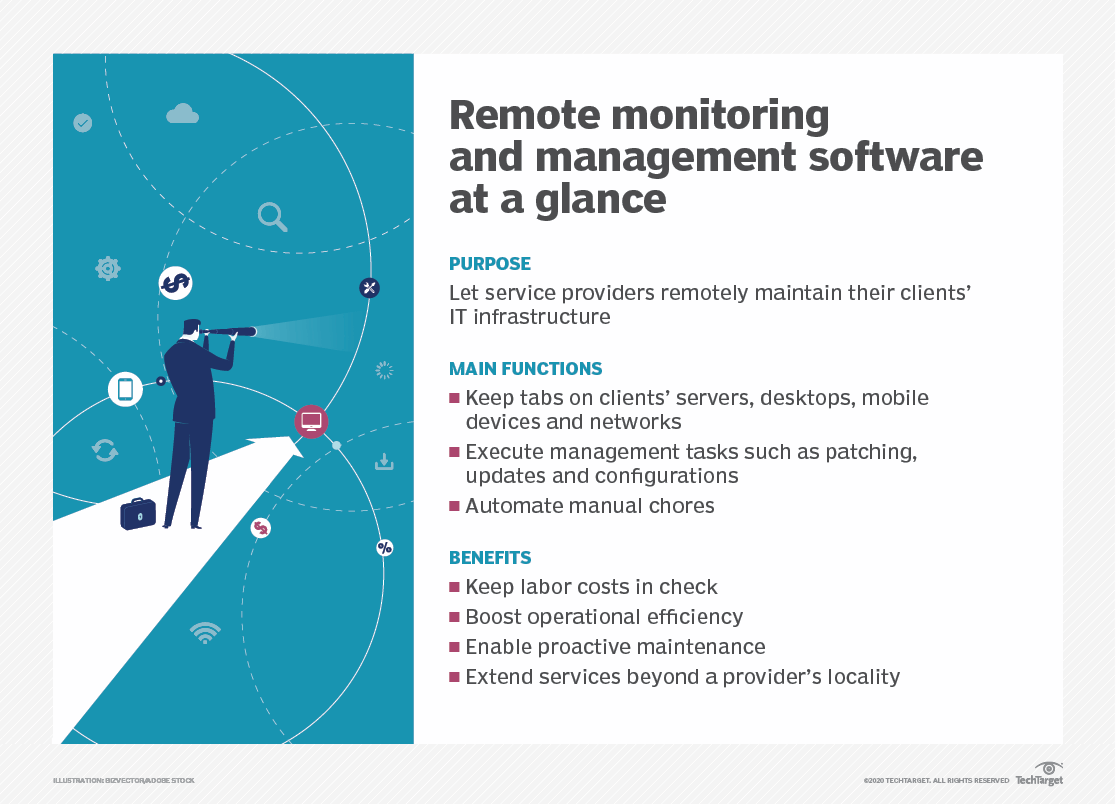
Remote access plays a crucial role in Remote Monitoring and Management (RMM) by facilitating seamless connectivity between IT support teams and client systems. This capability not only enhances operational efficiency but also ensures that technical issues can be addressed swiftly and securely. In an era where businesses rely heavily on technology, the ability to provide immediate support from any location has become indispensable.The integration of remote access into RMM platforms significantly boosts the operational efficiency of IT departments.
With remote access, technicians can troubleshoot and resolve issues without the need for onsite visits, reducing both time and resource expenditure. This immediacy allows companies to minimize downtime, leading to improved productivity and overall satisfaction for both employees and clients.
Enhanced Response Times for IT Support
A key advantage of remote access is its ability to streamline response times for IT support requests. When a technical issue arises, time is of the essence, and remote access empowers IT teams to act quickly. The following points illustrate the benefits of reduced response times in IT support:
- Immediate access to systems allows for rapid diagnosis and troubleshooting, often resolving issues within minutes rather than hours.
- Remote tools such as screen sharing enable technicians to guide users through solutions in real-time, eliminating the back-and-forth of traditional support methods.
- Remote access reduces travel time for support staff, allowing them to assist multiple clients in a single day, thus optimizing manpower allocation.
The ability to respond promptly not only enhances user experience but also builds trust and reliability in the IT support process.
Security Considerations Associated with Remote Access Solutions
While remote access offers numerous benefits, it also presents security challenges that must be addressed to protect sensitive data. It is essential to implement robust security measures to mitigate potential risks. Key considerations include:
- Utilization of strong authentication methods, such as two-factor authentication (2FA), to safeguard access to systems.
- Deployment of encrypted connections to ensure that data transmitted during remote sessions is secure from interception.
- Regular audits and logging of remote access sessions to track activities and identify any unauthorized access attempts.
By addressing these security concerns proactively, organizations can leverage the advantages of remote access while maintaining the integrity and confidentiality of their data.
Effective security measures are crucial for enabling safe remote access, ensuring that convenience does not compromise data integrity.
Tools and Technologies for Remote Access in RMM
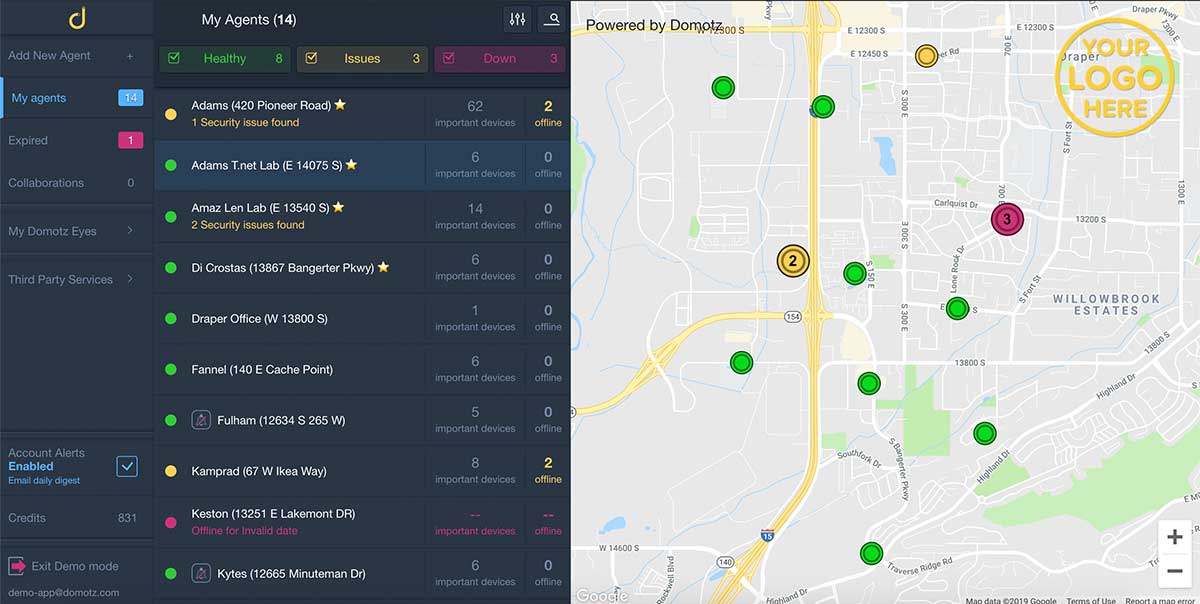
Remote access is a crucial component of Remote Monitoring and Management (RMM) solutions, enabling IT professionals to manage devices effectively from any location. The right tools and technologies not only streamline workflows but also enhance the security and efficiency of IT operations. This section will delve into the popular software solutions that facilitate remote access, compare their features, and describe how these technologies can be integrated into existing systems.
Popular Software Solutions for Remote Access
The landscape of remote access tools is vast, with numerous options catering to different business needs. Below are some of the leading software solutions that have gained popularity for their effectiveness and user-friendliness:
- TeamViewer: Offers cross-platform access, file transfer, and robust security features, making it ideal for both personal and business use.
- AnyDesk: Known for its speed and low latency, AnyDesk provides a seamless remote desktop experience, particularly for graphics-intensive applications.
- LogMeIn: Provides comprehensive remote access features, including remote printing and file sharing, suitable for larger enterprises.
- RemotePC: Focuses on providing a straightforward and cost-effective solution, with features such as multi-device access and collaboration tools.
- ConnectWise Control: Tailored for IT support teams, it offers advanced features such as session recording and unattended access capabilities.
Comparison of Features Among Leading Remote Access Tools
When selecting a remote access tool, it is essential to evaluate the features that align with specific needs. Below is a comparison of key features offered by leading remote access solutions:
| Feature | TeamViewer | AnyDesk | LogMeIn | RemotePC | ConnectWise Control |
|---|---|---|---|---|---|
| Cross-Platform Support | Yes | Yes | Yes | Yes | Yes |
| File Transfer | Yes | Yes | Yes | Yes | No |
| Unattended Access | Yes | Yes | Yes | Yes | Yes |
| Secure Connection | Yes | Yes | Yes | Yes | Yes |
| Multi-Device Support | Yes | Yes | Yes | Yes | Yes |
Integration of Remote Access Technologies Within Existing Systems
Integrating remote access technologies into existing systems involves several steps to ensure seamless functionality and security. The following aspects are crucial for a successful integration process:
Assess Existing Infrastructure
Implementing RMM Best Practices is crucial for any organization aiming to enhance its IT management. By adhering to these guidelines, companies can optimize their resources and improve service delivery, leading to better overall performance. This focus not only streamlines processes but also sets a foundation for growth and innovation in the tech landscape.
Evaluate current IT systems and determine compatibility with selected remote access tools. Consider hardware, software, and network capabilities to ensure smooth integration.
Security Protocols
Implement necessary security measures such as firewalls, VPNs, and encryption to protect sensitive data during remote sessions. This step is vital to maintaining compliance with data protection regulations.
Understanding the Benefits of RMM can significantly transform how businesses approach their IT operations. Remote Monitoring and Management not only enhances system reliability but also reduces downtime, allowing teams to focus on strategic initiatives rather than reactive troubleshooting. This proactive stance is essential for any modern enterprise looking to stay competitive in a fast-paced environment.
User Training
Provide training for users and IT staff to familiarize them with new tools and best practices. This helps in optimizing the use of remote access technologies and minimizing potential security risks.
Monitoring and Support
After integration, continuously monitor the performance of remote access tools. Regular updates and support are essential for addressing any issues that may arise and ensuring the tools remain effective.By choosing the right tools and ensuring proper integration, organizations can enhance their remote access capabilities, ultimately leading to improved operational efficiency and better service delivery in the realm of RMM.
Best Practices for Implementing Remote Access in RMM
Establishing effective remote access protocols within Remote Monitoring and Management (RMM) systems is crucial for ensuring operational efficiency and security. As organizations increasingly depend on remote access for IT management, adopting best practices can significantly enhance efficiency, security, and user experience.
Step-by-step Guide to Establishing Remote Access Protocols
Creating robust remote access protocols is essential for protecting sensitive information while facilitating seamless connectivity. Here is a structured approach for establishing these protocols:
- Assess Needs: Understand the specific requirements of your organization, including the types of devices and services that will need remote access.
- Select Tools: Choose appropriate remote access software that aligns with your organization’s needs, considering compatibility, features, and user-friendliness.
- Establish User Roles: Define roles and permissions to ensure users have the appropriate level of access based on their responsibilities.
- Implement Authentication Measures: Employ multi-factor authentication (MFA) to strengthen security, requiring users to provide additional verification beyond just passwords.
- Configure Access Controls: Utilize firewalls and VPNs to restrict access to authorized users and devices, creating secure communication channels.
- Provide Training: Offer training sessions for all users on how to properly use remote access tools and the importance of security protocols.
- Monitor and Audit: Regularly review access logs and perform audits to detect any unauthorized access or suspicious activities.
Training Requirements for Staff Using Remote Access Tools
Effective training is key to optimizing the use of remote access tools and ensuring staff members can operate them securely. Organizations should focus on comprehensive training sessions that cover the following aspects:
Training should not only focus on tool usage but also highlight the importance of security and compliance.
- Tool Proficiency: Staff must understand how to navigate and utilize remote access tools effectively.
- Security Awareness: Educate employees on potential security threats, such as phishing attacks and how to avoid them.
- Best Practices: Teach employees about password management, secure data handling, and the importance of keeping software updated.
- Incident Response: Provide guidelines on how to respond to security incidents and whom to contact within the organization.
Checklist for Evaluating Remote Access Security Measures, Remote Access in RMM
A comprehensive checklist is crucial for assessing the effectiveness of remote access security measures. This checklist can help organizations identify vulnerabilities and strengthen their defenses:
This checklist serves as a fundamental tool to ensure remote access security is regularly evaluated and improved.
- Is multi-factor authentication implemented for all remote access?
- Are access controls in place to restrict user permissions based on roles?
- Is sensitive data encrypted both in transit and at rest?
- Are regular security audits and vulnerability assessments conducted?
- Is there a clear incident response plan for remote access breaches?
- Are staff trained regularly on the latest security practices and tools?
- Is remote access monitored continuously for unauthorized access attempts?
Challenges and Solutions in Remote Access for RMM: Remote Access In RMM
Implementing remote access solutions in Remote Monitoring and Management (RMM) environments presents various challenges that organizations must navigate. As businesses increasingly rely on remote access for efficient IT management, understanding these obstacles and developing effective strategies to address them is essential.One of the primary challenges faced by organizations is security. Remote access can introduce vulnerabilities, making systems more susceptible to cyber threats.
Data breaches can occur if proper security measures are not in place. To mitigate these risks, organizations should prioritize strong authentication methods, such as multi-factor authentication (MFA), which adds an extra layer of security by requiring users to verify their identity through different means.
Common Obstacles in Implementing Remote Access Solutions
Organizations often encounter several notable challenges when implementing remote access solutions. Recognizing these issues allows for better planning and execution. The following points detail these common obstacles:
- Network Reliability: Unstable internet connections can hinder remote access, leading to disrupted services and lower productivity.
- Compatibility Issues: Different devices and operating systems may not always work seamlessly with remote access tools, complicating deployment.
- User Resistance: Employees may resist using remote access due to fear of change or concerns about privacy and security.
- Training Requirements: Proper training is essential for users and IT staff to maximize the effectiveness of remote access tools, which can be time-consuming.
Strategies to Mitigate Risks Associated with Remote Access
To effectively address the challenges of remote access, organizations can implement various strategies. These strategies not only enhance security but also improve user experience and operational efficiency. Security measures play a critical role in protecting sensitive information. Important strategies include:
- Implementation of VPNs: Using Virtual Private Networks (VPNs) encrypts data transmitted over the internet, ensuring secure connections.
- Regular Software Updates: Keeping remote access tools and software up to date helps protect against vulnerabilities and exploits.
- Access Controls: Limiting access to sensitive systems based on user roles helps minimize the risk of unauthorized access.
- Monitoring and Auditing: Continuous monitoring of remote access activities allows organizations to detect unusual behavior and respond promptly.
Case Studies of Organizations Overcoming Remote Access Challenges
Real-world examples illustrate how organizations successfully navigate remote access challenges. These case studies highlight effective solutions and adaptations.For instance, a mid-sized financial services company faced frequent security incidents related to remote access. To combat this, they implemented a robust MFA system and transitioned to a zero-trust security model, significantly reducing unauthorized access incidents. As a result, they improved their overall security posture while allowing employees secure access to necessary resources.Another case involves a technology firm that struggled with user resistance to remote access tools.
By conducting comprehensive training sessions and soliciting user feedback, they improved user confidence and satisfaction. This shift led to higher adoption rates and increased productivity, demonstrating the importance of user engagement in successful remote access implementation.Through understanding these challenges and implementing effective solutions, organizations can optimize their remote access strategies in RMM environments.