Patch Management via RMM is a critical component for organizations seeking to enhance their IT security landscape. Understanding the intricacies of patch management illuminates its importance in safeguarding systems, maintaining performance, and ensuring compliance in an ever-evolving digital environment. Whether addressing vulnerabilities or optimizing system functionalities, effective patch management is vital in protecting against potential threats.
This process involves not just the application of various types of patches but also the strategic deployment of Remote Monitoring and Management (RMM) tools, which simplify patching workflows. By leveraging RMM capabilities, IT teams can streamline their operations, prioritize tasks, and ensure regular updates, paving the way for improved system integrity and reduced risk.
Understanding Patch Management: Patch Management Via RMM
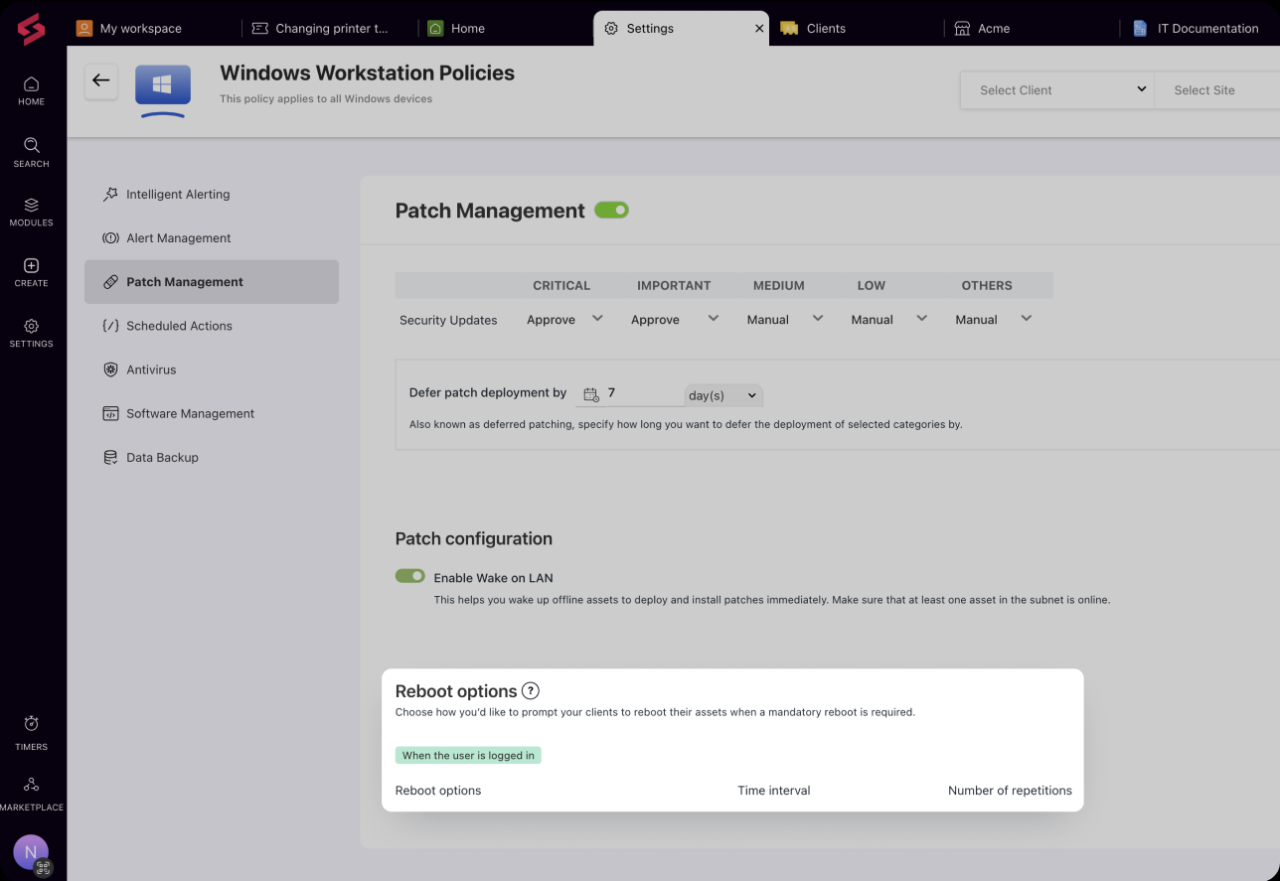
Patch management is a vital process in the realm of IT security, focusing on the systematic handling of updates and patches for software applications and systems. In a rapidly evolving technology landscape, organizations must ensure their systems are fortified against vulnerabilities, which can be exploited by cybercriminals. This process not only addresses security risks but also enhances system performance and compliance with regulatory standards.Patches are crucial updates provided by software vendors to fix known issues, improve functionality, or enhance security.
Understanding the various types of patches is essential for effective patch management. Generally, patches can be categorized into several types, each serving distinct purposes.
Types of Patches and Their Purposes, Patch Management via RMM
The importance of recognizing different types of patches lies in their specific roles in maintaining system integrity and performance. Below is a comprehensive overview of the types of patches encountered in IT management:
- Security Patches: These are released to address vulnerabilities that could be exploited by attackers. Regular application of security patches is critical for protecting sensitive data and maintaining system security.
- Bug Fixes: These patches resolve specific bugs or issues that affect software performance. By applying bug fixes, organizations can improve the overall functionality and reliability of their software.
- Feature Updates: These patches introduce new features or enhancements to existing functionalities. They help organizations to leverage advancements in technology to remain competitive.
- Service Packs: Comprehensive updates that bundle multiple patches, feature updates, and bug fixes into a single package. Service packs simplify the update process and ensure that systems are up-to-date.
The role of regular patch management extends beyond merely applying these patches. It is a proactive measure that ensures systems are not only secure but also operating at optimal performance levels. By regularly managing patches, organizations can significantly reduce the risk of security breaches, mitigate downtime, and improve user satisfaction.
Role of Regular Patch Management
Regular patch management plays a pivotal role in maintaining the integrity of IT systems. The following points underscore its significance:
- System Integrity: Consistent application of patches helps to maintain the integrity of systems by safeguarding against vulnerabilities that can compromise data and operations.
- Enhanced Performance: By fixing bugs and optimizing applications, patch management contributes to improved system speed and reliability, resulting in a better user experience.
- Compliance: Many industries face strict regulatory requirements. Regular patch management ensures alignment with compliance standards, minimizing the risk of legal penalties.
- Cost-Efficiency: Proactive patch management can prevent costly security incidents and system failures, making it a financially sound strategy for organizations.
“An ounce of prevention is worth a pound of cure.” This adage holds particularly true in the context of patch management, emphasizing the importance of proactive measures in preventing potential threats.
In conclusion, understanding patch management and its various types is essential for organizations aiming to protect their IT environments effectively. Regular patch management not only secures systems against vulnerabilities but also enhances overall performance, ensuring that organizations can operate smoothly and securely in a digital world fraught with risks.
RMM Tools and Their Features
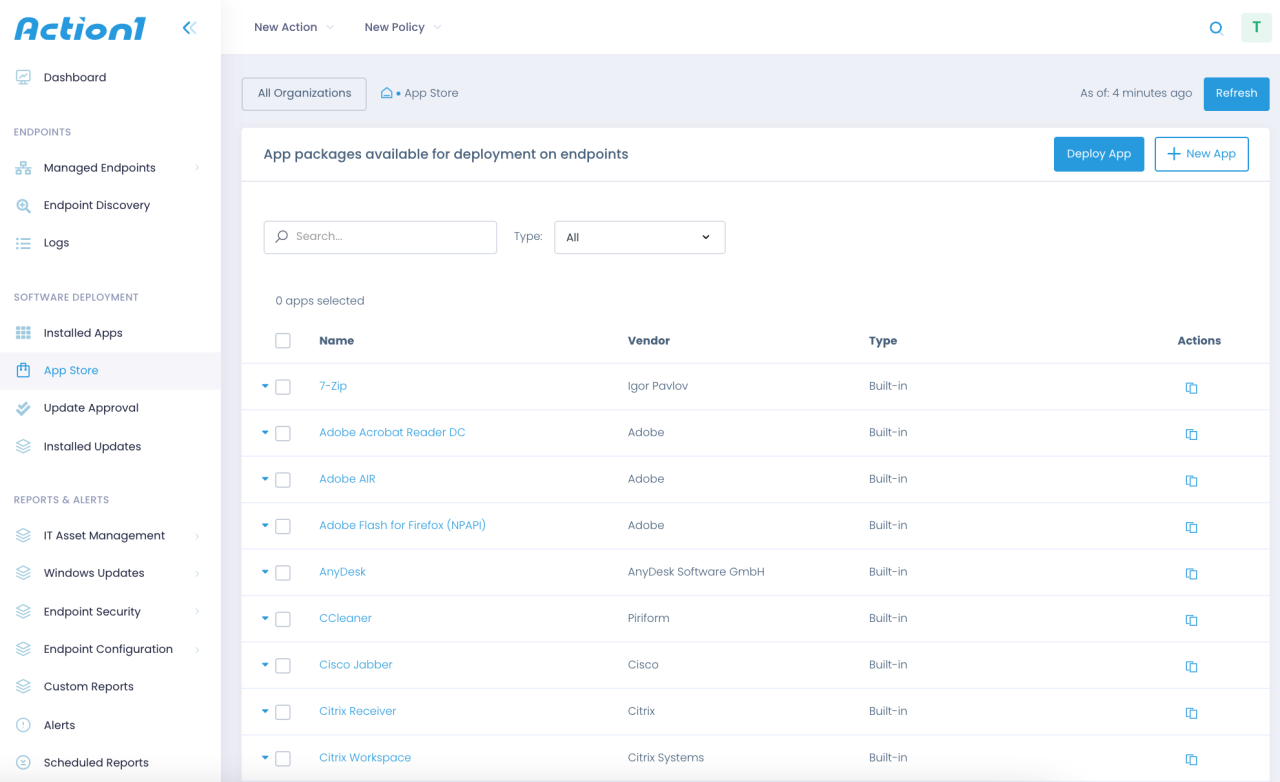
Remote Monitoring and Management (RMM) tools are essential for IT teams tasked with overseeing numerous endpoints and ensuring their security and functionality. A pivotal aspect of these tools is their patch management capabilities, which play a vital role in maintaining system integrity and preventing vulnerabilities. By automating and streamlining patch deployment, RMM tools not only save time but also enhance overall network security.RMM tools come equipped with a variety of features specifically designed to simplify the patch management process.
These features facilitate efficient monitoring, deployment, and reporting of patches across multiple systems, ultimately reducing the risk of security breaches and system failures. Below are key features associated with RMM tools that significantly contribute to effective patch management.
Key Features of RMM Tools for Patch Management
The following features of RMM tools are critical in enhancing patch management processes within IT teams:
- Automated Patch Deployment: RMM tools can schedule and automate the deployment of patches, ensuring that systems are updated without manual intervention.
- Comprehensive Reporting: They provide detailed reports on patch status, compliance levels, and any vulnerabilities, allowing IT teams to make informed decisions.
- Real-time Monitoring: RMM tools enable continuous monitoring of endpoints, providing alerts for any issues related to patch application.
- Rollback Capabilities: In the event that a patch causes issues, many RMM tools offer rollback features to revert systems to previous states.
- Multi-Platform Support: They support various operating systems and applications, allowing for consistent patch management across heterogeneous environments.
Comparison of Popular RMM Tools
To understand the competitive landscape of RMM tools, the following table compares popular solutions and their respective capabilities related to patch management. This comparison highlights the strengths and weaknesses of each tool.
If you’re new to the world of remote management, starting with RMM for Beginners can provide a solid foundation. This guide will help you navigate the essential tools and practices needed to optimize your management processes. Embracing RMM from the ground up empowers individuals and teams to harness technology effectively, leading to improved operational success.
| RMM Tool | Automated Deployment | Reporting Features | Rollback Capability | Multi-Platform Support |
|---|---|---|---|---|
| ConnectWise Automate | Yes | Advanced | Yes | Windows, Mac, Linux |
| Datto RMM | Yes | Standard | No | Windows, Mac |
| SolarWinds RMM | Yes | Detailed | Yes | Windows, Mac |
| ManageEngine Desktop Central | Yes | Comprehensive | Yes | Windows, Mac, Linux |
| NinjaRMM | Yes | Basic | No | Windows, Mac |
Streamlining Patch Management Processes
RMM tools significantly streamline the patch management process for IT teams by automating repetitive tasks and providing centralized control over updates. With the integration of these tools, organizations can quickly identify vulnerabilities and ensure timely patch application, which is crucial for safeguarding against exploitable security flaws.One notable advantage of RMM tools is their ability to deliver updates across various endpoints without the need for extensive manual effort.
This automation not only reduces the workload on IT staff but also minimizes the potential for human error during the update process. Additionally, the real-time monitoring capabilities of RMM tools allow IT teams to react swiftly to any issues arising from patch deployments, thereby maintaining system stability.Furthermore, the comprehensive reporting features available in many RMM solutions enable organizations to maintain compliance with industry standards and regulations.
For small businesses looking to streamline their operations, understanding RMM for Small Business is essential. This approach allows these enterprises to manage their resources effectively, ensuring maximum efficiency and productivity. By implementing RMM solutions tailored for smaller operations, businesses can significantly enhance their service delivery while keeping costs in check.
By regularly assessing the patch status of all devices on the network, IT teams can ensure that they are meeting their security obligations and protecting sensitive data.Overall, the integration of RMM tools into patch management strategies provides organizations with a proactive approach to IT security and operational efficiency, ultimately fostering a more resilient IT infrastructure.
Best Practices for Effective Patch Management
Implementing an effective patch management strategy is crucial for maintaining the security and functionality of an organization’s IT infrastructure. In an era where cyber threats are rampant and software vulnerabilities can lead to significant data breaches, having a well-structured approach to patch management can safeguard sensitive information and ensure operational continuity.A successful patch management strategy involves multiple facets, including timely updates, risk assessment, and consistent monitoring.
The following best practices Artikel essential steps organizations can take to enhance their patch management efforts.
List of Best Practices
Establishing a robust patch management process requires adherence to a series of best practices that not only streamline the patching process but also minimize associated risks. Consider the following practices:
- Develop a Patch Management Policy: Formulate a clear and comprehensive policy that defines the scope, roles, and responsibilities related to patch management. This policy should establish guidelines for testing, deployment, and documentation.
- Automate Patch Management: Utilize tools that can automate the patch management process, reducing the likelihood of human error and ensuring timely updates across all devices and systems.
- Regularly Inventory Assets: Maintain an updated inventory of all hardware and software assets. Knowing what needs patching is crucial for effective management.
- Prioritize Patches: Not all patches are created equal. Assess the severity of vulnerabilities and prioritize patches based on risk levels, focusing on those that could potentially lead to data breaches or operational disruptions.
- Test Patches Before Deployment: Ensure that patches are thoroughly tested in a controlled environment before being rolled out to avoid system conflicts or disruptions in operations.
- Schedule Regular Maintenance Windows: Establish specific times for deploying patches to minimize disruption to business operations, ideally during off-peak hours.
- Monitor and Document the Process: Keep detailed records of which patches have been applied, when, and to which systems. This documentation assists in auditing and compliance.
- Educate Staff: Conduct training sessions for IT staff about the importance of patch management and the potential consequences of neglecting updates.
Importance of Scheduling and Prioritizing Patches
Scheduling and prioritizing patches are critical components of an effective patch management strategy. By systematically arranging patch deployment, organizations can minimize downtime and prevent disruptions in service delivery. Prioritization ensures that the most critical vulnerabilities are addressed first, based on factors such as the potential impact on business operations and the exploitability of the threat.For instance, a patch that addresses a zero-day vulnerability—one that is actively being exploited—should be prioritized over non-critical updates.
This approach not only mitigates risks but also ensures that resources are allocated efficiently, allowing organizations to maintain productivity while enhancing security.
Potential Risks of Neglecting Patch Management
Neglecting patch management can expose an organization to numerous risks, which can have severe consequences. Failure to apply timely patches can lead to vulnerabilities being exploited by cybercriminals, resulting in data breaches, financial losses, and reputational damage. For example, the Equifax data breach in 2017 was partly attributed to unpatched vulnerabilities in their software. This incident led to the exposure of sensitive information from approximately 147 million consumers, underscoring the importance of diligent patch management.In addition to security risks, neglecting patches can result in decreased system performance and increased operational costs due to the potential need for emergency fixes or system recoveries.
Organizations must recognize that proactive patch management is not just a technical issue but a critical component of their overall risk management strategy.
Compliance and Regulatory Considerations
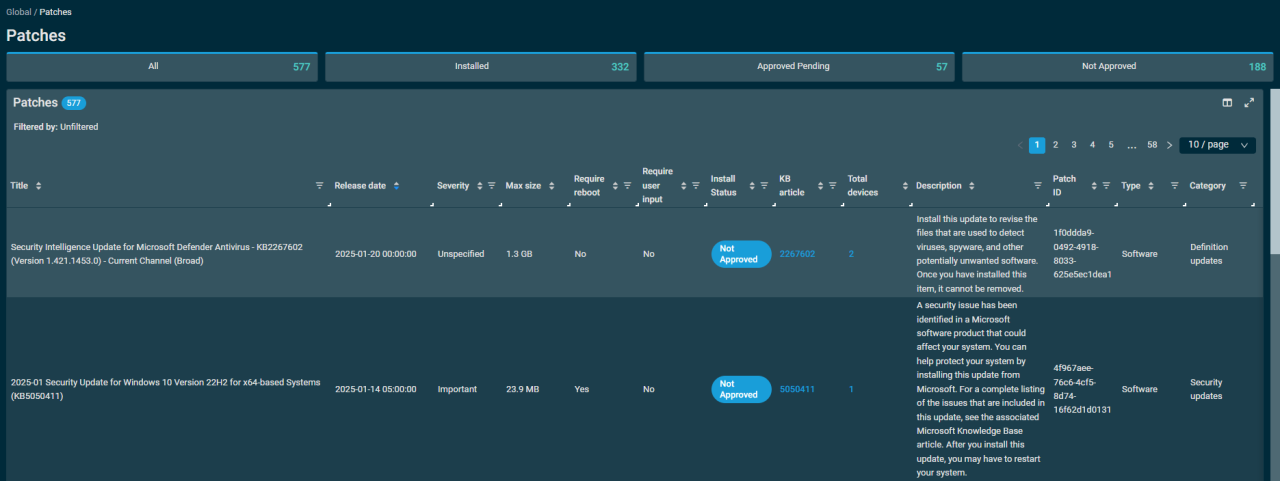
In today’s digital landscape, compliance and regulatory frameworks play a crucial role in shaping patch management strategies across various industries. Organizations must navigate a complex web of standards and regulations to ensure they maintain compliance while effectively managing software vulnerabilities. This section delves into the compliance requirements related to patch management and highlights how organizations can align their practices with these mandates.
Compliance Requirements in Various Industries
Different industries have unique compliance and regulatory requirements that impact patch management processes. Organizations must understand these requirements to avoid penalties and maintain operational integrity. Key regulations include:
- Health Insurance Portability and Accountability Act (HIPAA): This U.S. regulation requires healthcare organizations to protect patient information. Regular patching of systems and applications is essential to safeguard sensitive data from breaches.
- Payment Card Industry Data Security Standard (PCI DSS): Organizations that handle credit card transactions must adhere to PCI DSS, which mandates regular software updates and patching to protect cardholder data against vulnerabilities.
- Federal Information Security Management Act (FISMA): This U.S. federal law requires government agencies and contractors to implement security measures, including timely patch management, to protect federal information systems.
- General Data Protection Regulation (GDPR): As a comprehensive data protection regulation in the EU, GDPR emphasizes the need for organizations to ensure the security of personal data through effective patch management practices.
The adherence to these regulations not only ensures compliance but also enhances the overall security posture of an organization.
Ensuring Compliance Through Effective Patch Management Practices
To ensure compliance with regulatory requirements, organizations must implement effective patch management practices. A systematic approach can help mitigate risks associated with unpatched vulnerabilities and ensure adherence to relevant regulations. Essential practices include:
- Regular Patch Audits: Conducting periodic audits allows organizations to assess compliance with patch management policies and identify any gaps that need to be addressed.
- Automated Patch Management Tools: Utilizing RMM tools can streamline the patching process, ensuring timely deployment of updates and minimizing human error.
- Documentation and Reporting: Maintaining detailed records of patching activities is crucial for compliance. Organizations should document patch deployment schedules, actions taken, and results of patch audits.
- Employee Training: Educating employees about the importance of patch management and compliance helps foster a culture of security within the organization.
By integrating these practices into their operational frameworks, organizations can effectively manage patches while meeting regulatory requirements.
Summary of Regulations Impacting Patch Management Processes
Numerous regulations impact patch management processes, each emphasizing different aspects of information security and software management. A summary of key regulations includes:
| Regulation | Key Requirements |
|---|---|
| HIPAA | Protection of patient data, regular software updates |
| PCI DSS | Secure handling of cardholder data, timely patching |
| FISMA | Security measures for federal information systems, compliance audits |
| GDPR | Protection of personal data, security measures including patching |
Understanding and adhering to these regulations is vital for organizations to mitigate risks and enhance their cybersecurity frameworks through effective patch management.