Zero Trust with RMM sets the stage for a revolutionary approach in network security, where trust is never assumed and verification is paramount. This model shifts the traditional security mindset by emphasizing the necessity for continuous validation of every user and device, ensuring that only authorized entities can access sensitive data and systems. With the growing reliance on Remote Monitoring and Management, integrating Zero Trust principles becomes crucial to safeguarding network environments against evolving threats.
The essence of Zero Trust lies in its core principles: never trust, always verify. Within this framework, RMM tools play a vital role in monitoring and managing devices remotely, allowing organizations to maintain a strong security posture. The implications for network security are profound, as Zero Trust forces a reevaluation of how access is granted, monitored, and managed in real-time.
Definition and Importance of Zero Trust with RMM
Zero Trust is an essential security model that embodies the principle of “never trust, always verify.” This approach redefines traditional security paradigms by assuming that threats could exist both within and outside the network. When combined with Remote Monitoring and Management (RMM) systems, Zero Trust not only strengthens security postures but also enhances operational efficiency and resilience against cyber threats.
The core principles of Zero Trust revolve around strict identity verification, minimal access, and continuous monitoring. It requires that every user and device be authenticated and authorized before granting access to resources. This is particularly vital in RMM environments, where IT teams need to manage and monitor devices remotely, ensuring that only verified entities can interact with critical systems.
Significance of Remote Monitoring and Management within Zero Trust, Zero Trust with RMM
Implementing RMM within a Zero Trust framework is crucial for modern enterprises, given the rising sophistication of cyber threats. RMM solutions enable IT administrators to monitor networks and systems in real-time, applying patches, managing updates, and addressing vulnerabilities proactively. The integration of RMM with Zero Trust principles emphasizes the following key aspects:
- Enhanced Visibility: RMM tools allow organizations to gain insights into device status, performance, and security vulnerabilities. This visibility is instrumental in identifying potential threats before they escalate.
- Continuous Authentication: Zero Trust mandates continuous verification of user identities and device integrity. RMM solutions can enforce multi-factor authentication (MFA) and device compliance checks to ensure that only secure devices access sensitive information.
- Automated Response: RMM systems enable automated responses to detected anomalies, such as unauthorized access attempts. This swift action minimizes the risk of data breaches and system compromises.
- Granular Access Control: Zero Trust promotes the principle of least privilege, ensuring users only have access to the resources necessary for their roles. RMM solutions can segment access based on user roles, applying stringent access controls to sensitive areas of the network.
- Resilience Against Insider Threats: By continuously monitoring activities and behaviors within the network, RMM tools can detect insider threats, such as compromised accounts or malicious activities by authorized users.
The implications of Zero Trust for network security in RMM environments are profound. Organizations adopting this model can expect increased protection against cyber attacks, improved compliance with regulatory requirements, and a robust framework for managing remote operations securely. As organizations continue to embrace digital transformation, the synergy between Zero Trust and RMM will play a pivotal role in safeguarding their assets and data.
RMM Alert Fatigue has become a significant challenge for IT teams, leading to a decrease in response effectiveness. As alerts multiply, the risk of overlooking critical notifications increases. Addressing this issue is essential for maintaining operational efficiency, and understanding the nuances of RMM Alert Fatigue can help organizations implement better strategies to manage their alerts.
Key Components of Zero Trust Architecture: Zero Trust With RMM
Zero Trust architecture represents a paradigm shift in cybersecurity, moving away from perimeter-based defenses to a framework that assumes threats could be both internal and external. This model emphasizes the need for strict identity verification and continuous monitoring regardless of the user’s location. Understanding the key components of Zero Trust is essential for organizations looking to enhance their security posture.The essential elements of a Zero Trust architecture can be categorized into several critical components that work synergistically to protect data and resources.
Each element plays a specific role in enforcing the Zero Trust principles of least privilege access and continuous validation.
In today’s digital workplace, the integration of BYOD and RMM has transformed how companies manage their IT resources. By allowing employees to use personal devices, organizations can enhance productivity, but it also raises security concerns. Effective remote monitoring and management (RMM) solutions are crucial to ensure that these devices are secure and compliant, bridging the gap between flexibility and safety.
Essential Elements of Zero Trust Architecture
Implementing Zero Trust requires a thorough understanding of its key components. These elements form the foundation of a robust security framework:
- Identity and Access Management (IAM): IAM solutions are vital for managing user identities and governing their access to resources. They ensure that only authenticated and authorized users can access specific data and applications.
- Device Security: All devices seeking access to the network must meet certain security standards. This includes ensuring devices are compliant with security policies and are regularly updated.
- Network Segmentation: Dividing the network into smaller segments limits lateral movement within the network. This ensures that if a breach occurs, it can be contained within a limited area.
- Data Protection: Encrypting sensitive data both at rest and in transit safeguards it against unauthorized access. This is crucial for maintaining data integrity.
- Monitoring and Analytics: Continuous monitoring of user activities and network traffic provides real-time insights and helps identify anomalies or potential threats swiftly.
Integrating RMM Tools Within a Zero Trust Strategy
Remote Monitoring and Management (RMM) tools play a significant role in the Zero Trust framework by enabling organizations to maintain visibility and control over their IT environments. Integration of RMM tools within a Zero Trust strategy ensures that device security and compliance are continuously monitored.To effectively integrate RMM tools within this framework, organizations should consider the following approaches:
- Real-time Device Monitoring: RMM tools provide real-time visibility into device health and performance, allowing for immediate detection of any discrepancies that may indicate a security threat.
- Patch Management: Automated patch management through RMM tools ensures that all devices are regularly updated with the latest security patches, reducing vulnerabilities.
- Policy Enforcement: Organizations can leverage RMM tools to enforce security policies consistently across all devices, ensuring compliance with the Zero Trust model.
- Incident Response: RMM tools facilitate a rapid response to security incidents by providing detailed logs and analytics, helping teams to understand and mitigate threats quickly.
The Role of Identity and Access Management in a Zero Trust Model
Identity and Access Management (IAM) is a cornerstone of the Zero Trust model, as it directly enforces the principle of ‘never trust, always verify.’ IAM solutions are essential for controlling user identities and access levels, ensuring that each user has the minimum required permissions to perform their tasks.The importance of IAM in a Zero Trust architecture includes:
- Multi-Factor Authentication (MFA): MFA adds an additional layer of security by requiring users to provide two or more verification factors, greatly reducing the likelihood of unauthorized access.
- Granular Access Control: IAM solutions allow organizations to implement fine-grained access controls based on user roles, contexts, and risk levels, ensuring that users can only access the data necessary for their roles.
- Single Sign-On (SSO): SSO simplifies the user experience while maintaining security by reducing the number of login credentials needed, minimizing the risk of password fatigue.
- Continuous Authentication: Continuous validation of user identities through behavioral analytics ensures that users are consistently verified throughout their sessions, responding to any suspicious activity in real-time.
Challenges in Implementing Zero Trust with RMM
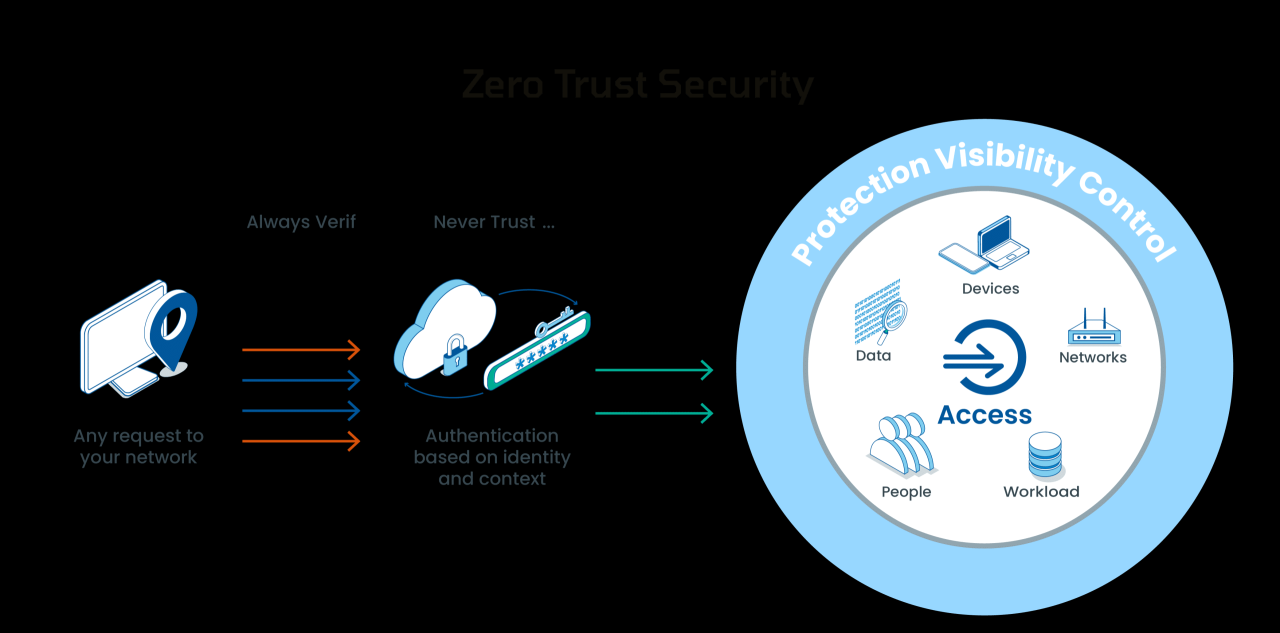
The adoption of a Zero Trust security model in conjunction with Remote Monitoring and Management (RMM) solutions presents various challenges. As organizations strive to enhance their digital security posture, they often encounter multiple obstacles that can hinder the effective implementation of Zero Trust principles. Understanding these challenges is crucial for organizations to navigate the complexities of securing their IT environments while utilizing RMM tools.One of the primary hurdles in implementing Zero Trust with RMM is the complexity of existing infrastructure.
Organizations often rely on legacy systems that may not align with the granular security controls mandated by a Zero Trust framework. Additionally, the integration of RMM solutions into these environments can introduce potential risks, requiring a careful assessment of compatibility and security implications.
Obstacles in Adopting Zero Trust
Various obstacles can arise during the transition to a Zero Trust security model, particularly when integrating RMM solutions. Some of the most common challenges include:
- Legacy Systems Compatibility: Many organizations operate with older systems that lack the necessary features to support a Zero Trust architecture, making it difficult to enforce strict access controls.
- Resource Constraints: Limited budgets and personnel can impede the deployment of comprehensive security measures essential for a Zero Trust model, especially in organizations struggling with IT staffing.
- Cultural Resistance: Changing the mindset of employees and management regarding security practices can be challenging, as Zero Trust requires a shift from traditional security models that focus on perimeter defenses to a more holistic approach.
- Complexity of Integration: Integrating RMM tools with existing security frameworks can introduce additional complexity, leading to potential misconfigurations that expose organizations to cyber threats.
Potential Risks with RMM Integration
Integrating RMM solutions into an existing security framework under a Zero Trust model carries specific risks that organizations must address. These risks include:
- Data Exposure: RMM tools often require extensive access to systems and data, which can create vulnerabilities if not properly managed within a Zero Trust framework.
- Insider Threats: The broader access granted to RMM solutions may inadvertently increase the risk of insider threats, as employees or third-party vendors may exploit their access for malicious purposes.
- Configuration Errors: Incorrect configurations during the integration of RMM can lead to security gaps. A misconfigured RMM tool can inadvertently allow unauthorized access to sensitive data.
- Compliance Challenges: Ensuring that RMM deployments comply with industry regulations and standards becomes increasingly complex when adopting a Zero Trust approach.
Strategies to Overcome Implementation Hurdles
To successfully implement a Zero Trust model with RMM solutions, organizations can adopt several strategies to mitigate challenges and risks:
- Conduct a Thorough Assessment: Organizations should start with a comprehensive assessment of their existing infrastructure to identify legacy systems and potential vulnerabilities that need addressing before implementing Zero Trust.
- Develop a Phased Implementation Plan: A phased approach to deployment allows organizations to gradually introduce Zero Trust principles and RMM integration, enabling better management of resources and minimizing disruption.
- Enhance Employee Training: Ongoing training and awareness programs can help foster a security-first culture within the organization, ensuring that employees understand the importance of Zero Trust principles.
- Implement Robust Access Controls: Use advanced authentication methods and strict access controls tailored to user roles and responsibilities to minimize risk while utilizing RMM solutions.
Case Studies and Best Practices
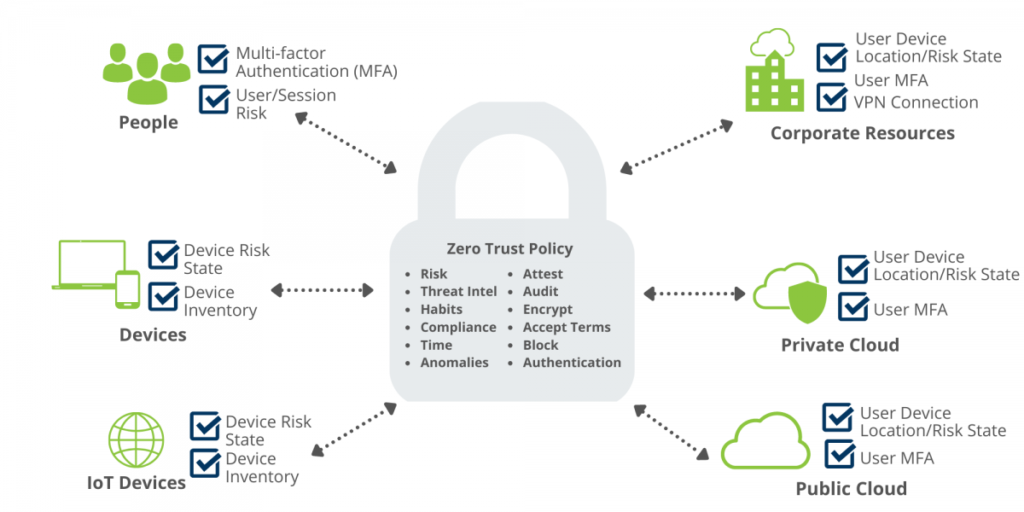
Numerous organizations have successfully adopted Zero Trust architecture in conjunction with Remote Monitoring and Management (RMM) solutions to enhance their security posture. This section explores detailed comparisons of these organizations, highlighting their strategies and outcomes. Additionally, it Artikels best practices for bolstering security through Zero Trust methodologies and provides guidance on evaluating the effectiveness of these implementations in remote management settings.
Successful Implementations of Zero Trust with RMM
Several organizations exemplify the successful integration of Zero Trust principles within their RMM frameworks. These case studies showcase varied approaches tailored to the specific needs of different industries.
1. Financial Institution A
Faced with stringent regulations, Financial Institution A implemented a Zero Trust model focusing on user identity verification and continuous monitoring of network traffic. By utilizing RMM tools, they ensured that access to sensitive data was restricted to verified users only, resulting in a significant decrease in unauthorized access incidents.
2. Healthcare Provider B
Healthcare Provider B adopted a Zero Trust strategy to safeguard patient data against breaches. They leveraged RMM solutions to segment patient data and enforce stringent access controls. This multi-layered approach not only improved compliance with HIPAA regulations but also minimized the risk of data leaks.
3. Tech Company C
Tech Company C focused on securing its remote workforce by implementing Zero Trust principles through RMM. By continuously validating device security posture and user behavior, they effectively reduced the attack surface and improved incident response times, which led to a 40% reduction in security-related incidents.
Best Practices for Enhancing Security
Implementing Zero Trust methodologies within RMM environments necessitates adherence to certain best practices that can significantly enhance security.To effectively bolster security using Zero Trust principles in RMM, organizations should consider the following practices:
Continuous Monitoring and Analytics
Employ advanced analytics tools to continuously monitor user behavior and system activities. This proactive stance allows for the early detection of anomalies and potential security threats.
Micro-segmentation
Implement micro-segmentation strategies to isolate critical assets and limit lateral movement within the network. This reduces the potential impact of a breach by confining access to specific segments.
Least Privilege Access
Enforce a least privilege approach to user access, ensuring that users have only the permissions necessary to perform their job functions. Regularly review and adjust permissions based on role changes.
Multi-Factor Authentication (MFA)
Require MFA for all remote access to systems and applications. This adds an additional layer of security, making it more difficult for unauthorized users to gain access.
Comprehensive Incident Response Plan
Develop and maintain a robust incident response plan that incorporates Zero Trust principles. Regularly conduct drills to ensure readiness and efficiency in responding to security incidents.
Assessing Effectiveness of Zero Trust Implementations
Evaluating the effectiveness of Zero Trust architectures in RMM environments is crucial for understanding their impact on security posture. Organizations should consider various metrics and methodologies for this assessment.Key performance indicators (KPIs) to evaluate Zero Trust implementations may include:
Rate of Security Incidents
Track the number and severity of security incidents before and after Zero Trust implementation. A reduction in incidents would indicate effective security measures.
User Access Reviews
Regularly conduct audits of user access logs to ensure compliance with least privilege policies. This practice helps in identifying any anomalies in access patterns.
Incident Response Times
Measure the time taken to detect and respond to security incidents. A decrease in response times can reflect the effectiveness of continuous monitoring strategies.
Compliance Metrics
Assess compliance with industry regulations and standards. Successful adherence can demonstrate the effectiveness of Zero Trust practices in mitigating compliance risks.
User Feedback and Experience
Gather feedback from users regarding their experience with access controls and security measures. A balance between security and user experience is essential for the long-term success of Zero Trust implementations.By focusing on these areas, organizations can ensure that their Zero Trust frameworks effectively enhance the security of their RMM practices, ultimately leading to a more secure operational environment.